Kaspersky has unveiled a significant spike in activity from a malicious spam-email campaign, which spreads the dangerous malware Emotet and Qbot and targets corporate users. The number of such malicious emails grew from around 3,000 in February 2022 to approximately 30,000 in March. The campaign is likely connected to the increasing activity of the Emotet botnet.
Kaspersky experts have detected significant growth in complex malicious spam emails targeting organisations in various countries. These emails are being distributed as part of a coordinated campaign that aims to spread Qbot and Emotet – two notorious banking Trojans that function as part of botnet networks. Both malware instances are capable of stealing users’ data, collecting data on an infected corporate network, spreading further in the network, and installing ransomware or other Trojans on other devices in the network. One of the functions of Qbot is also to access and steal emails.
While this campaign has been ongoing for a few months, its activity increased rapidly from – 3,000 emails in February 2022 to – 30,000 in March. Malicious emails have been detected in the English, French, Hungarian, Italian, Norwegian, Polish, Russian, Slovenian and Spanish languages.
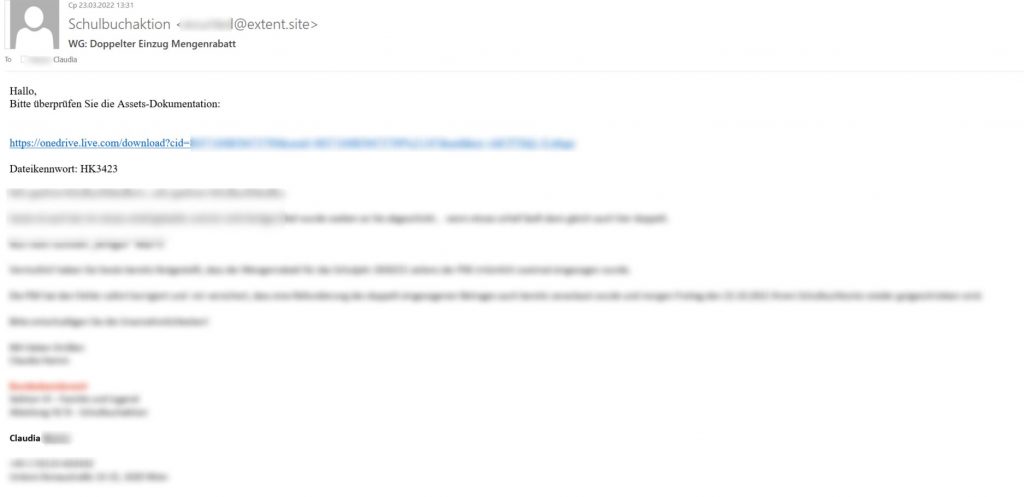
The malware-spreading campaign is structured as follows: cybercriminals intercept already existing correspondence and send the recipients an email containing a file or link, which often leads to a legitimate popular cloud-hosting service. The aim of the email is to convince users to either follow the link and download an archived document and open it – sometimes using a password mentioned in the email, or simply open an email attachment. To convince users to open or download the file the attackers usually state that it contains some important information, such as a commercial offer.
This archived document is detected by Kaspersky as HEUR:Trojan.MSOffice.Generic. In most cases it downloads and launches a Qbot dynamic library, but Kaspersky has also observed that some of these documents download Emotet instead.
Commenting on the campaign, Andrey Kovtun, security expert at Kaspersky, said: “Imitating work correspondence is a common trick employed by cybercriminals; however, this campaign is more complicated, since the attackers intercept an existing conversation and essentially insert themselves into it, which makes such messages harder to detect. While this scheme may resemble business email compromise attacks (BEC-attacks) – where the attackers pretend to be a colleague and have a conversation with the victim – here the attackers do not target specific individuals; business correspondence is just a smart way to increase the chances of the recipient opening the files.”
In order to stay safe from attacks by Qbot and Emotet, Kaspersky recommends the following:
- Checking the sender’s address. Most spam comes from email addresses that don’t make sense or appear as gibberish – for example, [email protected] or similar. By hovering over the sender’s name, which itself may be spelled oddly, you can see the full email address. If you’re not sure if an email address is legitimate or not, you can put it into a search engine to check.
- Being wary of the message creating a sense of urgency. Spammers often try to apply pressure by creating a sense of urgency. For example, the subject line may contain words like “urgent” or “immediate action required” – to pressure you into acting.
- Providing your staff with basic cybersecurity hygiene training; also conducting a simulated phishing attack to ensure that they know how to distinguish phishing emails and genuine ones.
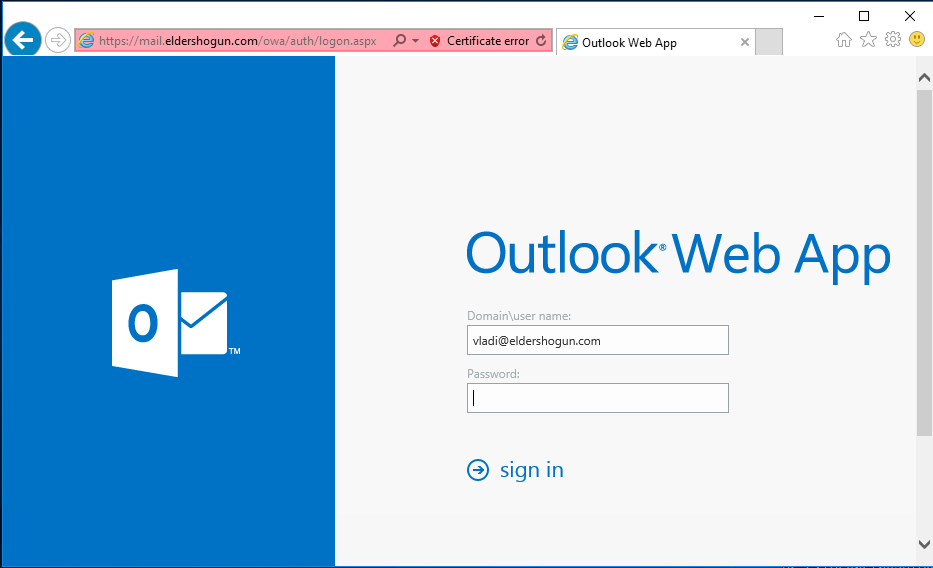
- Using a protection solution for endpoints and mail servers with anti-phishing capabilities, such as Kaspersky Endpoint Security for Business, to decrease the chance of infection through a phishing email.
- Installing a reliable security solution such as Kaspersky Secure Mail Gateway, which automatically filters out spam messages.
Read: Kenya’s Businesses Dealing With 1400 Cyberattacks Each Week
>>> Companies Continue Increasing Cybersecurity Budgets, Entire Market to Hit $158.8B Value by 2023










![The market for Internet of Things (IoT) devices has seen active growth recently – with a dramatic increase of 23.1% in 2020. [Photo/ Future Residence]](https://businesstoday.co.ke/wp-content/uploads/2021/09/Smart-Home-Automation1.jpeg)

Leave a comment