Kaspersky has uncovered a previously unknown IIS module (a piece of software aimed at providing additional features to Microsoft web servers) they have since dubbed Owowa that stęals credentials entered by a user when logging into Outlook Web Access (OWA). It also allows the attąckers to gain remote control access to the underlying server.
Compiled sometime between late 2020 and April 2021, this module is a stealthy thęft method that is difficult to detect with network monitoring. It’s also resistant to software updates from Exchange, meaning it can stay hidden on a device for a long time.
In 2021, advanced threat actors were increasingly exploiting vulnerabilities of Microsoft Exchange Server. In March, four critical vulnerabilities in the servers allowed attąckers to gain access to all registered email accounts and execute arbitrary code.
While searching for additional potentially malicious implants in Exchange, Kaspersky experts uncovered a malicious module that allows the attąckers to stęal login credentials for Outlook Web Access and gain remote access control to the underlying server. Kaspersky has dubbed this malicious module Owowa, and its malicious capabilities can easily be launched by sending seemingly innocuous requests – in this case, OWA authentication requests.
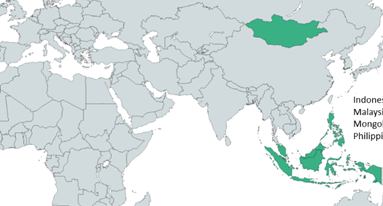
Kaspersky experts believe the module was compiled between late 2020 and April 2021, and it has been seen targeting victįms in Malaysia, Mongolia, Indonesia, and the Philippines. Most of the victįms were connected with government organisations and another to a state transportation company. It is likely there are additional victįms located in Europe.
The cybercriminals only need to access the OWA log-in page of a compromised server to enter specially crafted commands into the username and password fields. This is an efficient option for attąckers to gain a strong foothold in targeted networks by persisting inside an Exchange server.
Kaspersky researchers could not associate Owowa to any known threat actor. Yet, they did find that it was associated with the username “S3crt”, a developer that may be behind several other malicious binary loaders. However, “S3crt” is a simple derivation of the English word “secret” and could very well be used by multiple individuals. Therefore, it’s also possible that these malicious binary files and Owowa are not connected.
“The particular danger with Owowa is that an attącker can use the module to passively stęal credentials from users who are legitimately accessing web services. This is a far stealthier way to gain remote access than sending phishing emails. In addition, while IIS configuration tools can be leveraged to detect such threats, they are not part of standard file and network monitoring activities, so Owowa might be easily overlooked by security tools,” comments Pierre Delcher, Senior Security Researcher with Kaspersky’s Global Research and Analysis Team (GReAT).
“Since Owowa is an IIS module, this also means it persists even if Microsoft Exchange is updated. The good news is, the attąckers don’t appear highly sophisticated. Companies should closely monitor Exchange servers since they are highly sensitive and contain all corporate emails. We also recommend considering all running modules as critical and checking them regularly,” comments Paul Rascagneres Senior Security Researcher with Kaspersky’s GReAT.
To protect yourself from such threats, Kaspersky recommends:
- Regularly check loaded IIS modules on exposed IIS servers (notably Exchange servers), leveraging existing tools from the IIS servers suite. In any case, check for such modules as part of threat hunting activities, every time a major vulnerability is announced on Microsoft server products.
- Focus your defense strategy on detecting lateral movements and data exfiltration to the Internet. Pay special attention to outgoing traffic to detect cybercriminal connections. Back up data regularly. Make sure you can quickly access it in an emergęncy.
- Use solutions like Kaspersky Endpoint Detection and Response and the Kaspersky Managed Detection and Response service which help to identify and stop the attąck in the early stages before the attąckers achieve their goals.
- Use a reliable endpoint security solution such as Kaspersky Endpoint Security for Business that is powered by exploit prevention, behaviour detection and a remediation engine that is able to roll back malicious actions. KESB also has self-defense mechanisms that can prevent its removal by cybercriminals.
Read: How Simple Internet Skills Can Help SMEs Survive Coronavirus
>>> Fake Deliveries and Whatsapp Scams: Fraudsters’ Latest Tactics Revealed


![Health Cabinet Secretary Mutahi Kagwe. He confirmed the first case of the Omicron variant in Kenya. [Photo/ MoH]](https://businesstoday.co.ke/wp-content/uploads/2021/12/IMG-20201019-WA0021-150x150.jpg)







![The market for Internet of Things (IoT) devices has seen active growth recently – with a dramatic increase of 23.1% in 2020. [Photo/ Future Residence]](https://businesstoday.co.ke/wp-content/uploads/2021/09/Smart-Home-Automation1.jpeg)

Leave a comment