ESET, a leading global cyber security company, has discovered another set of malicious apps in the official Android app store.
Detected by ESET security systems as Android/TrojanDropper.Agent.BKY, the eight apps form a new family of legitimate-looking, multi-stage Android malware, and with delayed onset of malicious activity.
Eset has since notified Google’s security team about the issue. Google has removed all eight apps from its store; users with Google Play Protect enabled are protected via this mechanism.
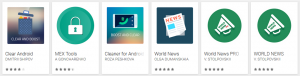
Figure 1 – Six of the multi-stage downloaders discovered on Google Play
Anti-detection features
None of the apps, that have advanced anti-detection features had reached more than a few hundred downloads. The malware samples all employed a multi-stage architecture and encryption to stay under the radar. After being downloaded and installed, the apps tended not to request any suspicious permissions and even mimic the activity the user expects them to exhibit.
Along with this, the malicious app also decrypts and executes its first-stage payload which in turn decrypts and executes the second-stage payload, which was then stored in the assets of the initial app downloaded from Google Play. The steps remained invisible to the user and served as obfuscatory measures.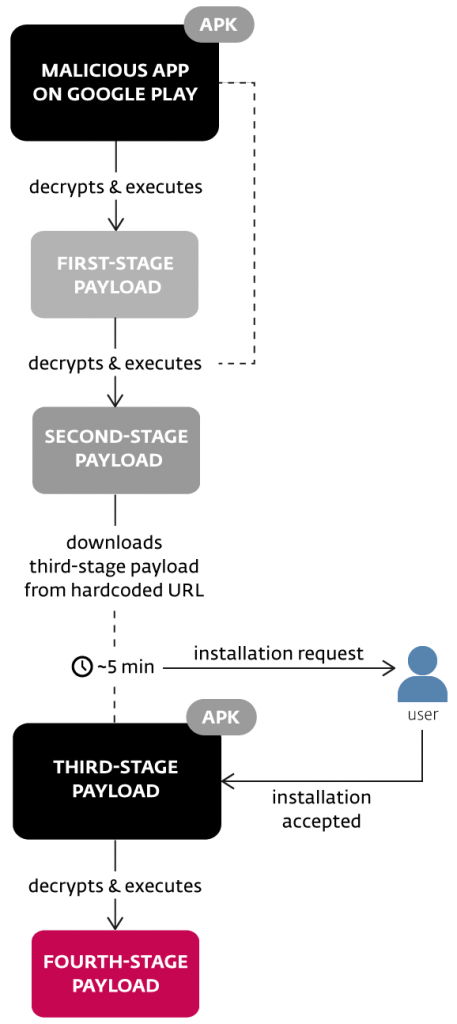
Figure 2 – Execution model of Android/TrojanDropper.Agent.BKY
The second-stage payload contained a hardcoded URL, from which it downloaded another malicious app (that is, the third-stage payload) without the victim’s knowledge. After a pre-defined delay of approximately five minutes, the user was then prompted to install the downloaded app.
READ: Stock market will weather political storm: NSE CEO
The app downloaded by the second-stage payload, disguised as well-known software like Adobe Flash Player or as something legitimate-sounding yet completely fictional – for example “Android Update” or “Adobe Update”. In any case, the app’s purpose was to drop the final payload and obtain all the permissions that payload needed for its malicious actions.
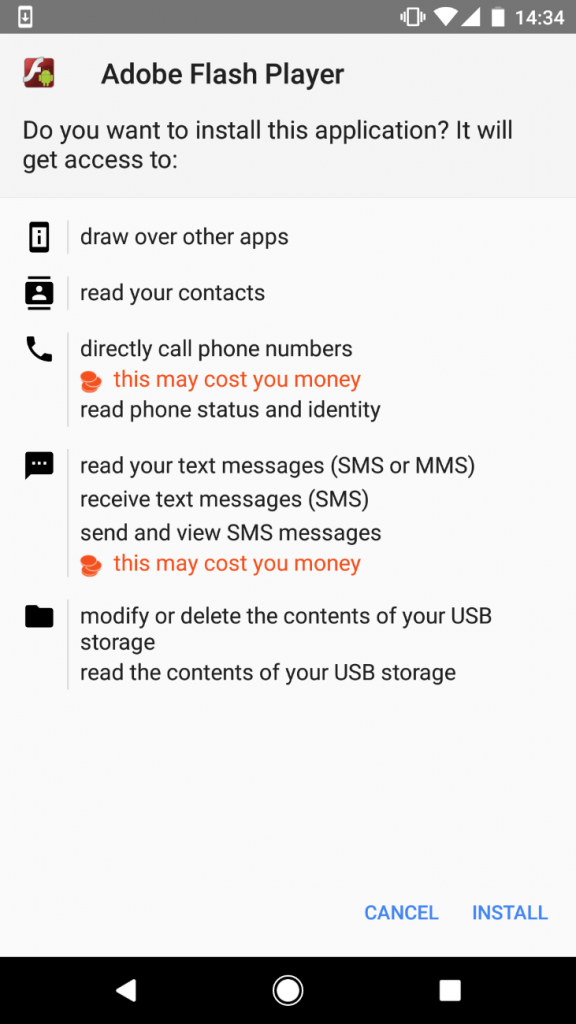
Once installed and having the requested permissions granted, the malicious app serving as the third-stage payload decrypted and executed the fourth-stage – and final – payload.
In all the cases investigated by ESET, the final payload was a mobile banking trojan. Once installed, it behaved like a typical malicious app of this kind: with potential to present the user with fake login forms to steal credentials or credit card details.
One of the malicious apps downloaded its final payload using the bit.ly URL shortener. Thanks to this, ESET was able to obtain download stats: as of November 14, 2017, the link had been used almost 3000 times with the vast majority of hits coming from the Netherlands.
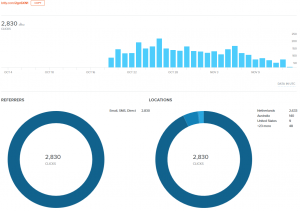
Figure 4 – Download stats for the final payload of one of the malicious apps, as of November 14, 2017
How to get rid of it
If you’ve downloaded any of these apps, you need to (i) deactivate admin rights for the installed payload, (ii) uninstall the surreptitiously-installed payload and (iii) uninstall the app downloaded from the Play Store.
To deactivate admin rights for the installed payload, go to Settings > (General) > Security > Device administrators and search for Adobe Flash Player, Adobe Update or Android Update.
To uninstall the installed payload, go to Settings > (General) > Application manager/Apps and search for the particular apps (Adobe Flash Player, Adobe Update or Android Update) to uninstall them.
To uninstall the malicious app downloaded from the Play store, go to Settings > (General) > Application manager/Apps and search for apps going by the following names: MEX Tools, Clear Android, Cleaner for Android, World News, WORLD NEWS, World News PRO.
Note that the settings structure may vary slightly depending on Android version.
How to stay protected
Unfortunately, multi-stage downloaders, with their improved obfuscation features, have a better chance of sneaking into official app stores than common Android malware does. Users who want to stay protected should not rely fully on the stores’ protections; instead, it’s crucial for users to check app ratings and comments, pay attention to what permissions they grant to apps, and run a quality security solution on their mobile devices.












Greetings from Carolina! I’m bored to tears at work so I decided to browse your blog on my iphone during lunch break.
I enjoy the information you present here and can’t wait to take a look when I get home.
I’m shocked at how quick your blog loaded on my cell phone ..
I’m not even using WIFI, just 3G .. Anyways, very good blog!
I love what you guys are up too. Such clever work
and exposure! Keep up the awesome works guys I’ve added you guys to my own blogroll.
I am actually thankful to the owner of this site who has shared this enormous
article at at this time.
I do not even know how I stopped up here, but I assumed
this submit used to be good. I don’t recognise who you are however definitely you are going
to a famous blogger in case you are not already. Cheers!
Superleuk informatief artikel met alle highlights opgesomd!
I always spent my half an hour to read this website’s posts
daily along with a cup of coffee.